Setting up full-disk encryption in OpenBSD 5.3
I recently decided to try out a snapshot of OpenBSD 5.3, intrigued by the notice that
softraid(4) RAID1 and crypto volumes are now bootable on i386 and amd64 (full disk encryption).
I’ve always used an encrypted LVM (as setup by the alternate CD) with a fully encrypted root on my netbook and laptop when running Debian/Kubuntu and never noticed much a performance hit. Unfortunately, I’m not the only one who has noticed a significant drop in performance with full-disk encryption on OpenBSD.
Although the steps required to setup full-disk encryption (as opposed
to requiring manual intervention at boot or the equivalent
of loop-mounted encrypted images via
vnconfig(8)) on OpenBSD are not explicitly documented
anywhere, searching through the mailing lists, man pages, and trial
and error provided the following steps:
- Boot from your install media. Select the
(S)helloption. - Assuming the disk you’re installing to is “
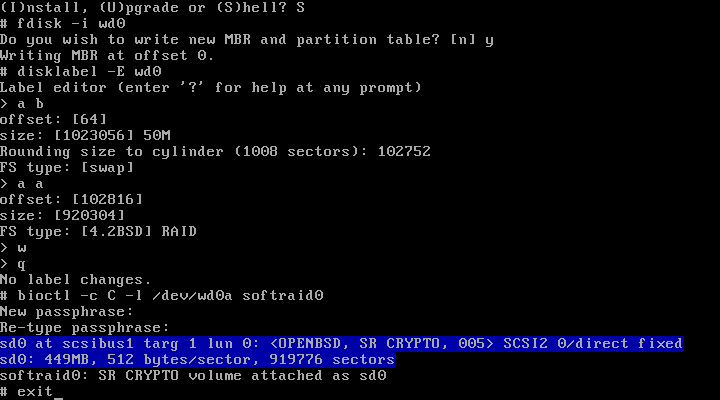
wd0”, runfdisk -i wd0if you’re on an i386. If I’m not mistaken, you can skip to the following step otherwise. - Run
disklabel -E wd0. Create a label (typicallyb) of the appropriate size of typeswapfor swap, and then add a labelausing the remainder of the space of typeRAID. We aren’t going to putswapon our crypto device since OpenBSD has encrypted the swap partition by default since 2005. - Setup the crypto volume as described in
bioctl(8). You will be prompted for a passphrase and presented with a message along the lines ofsoftraid0: SR CRYPTO volume attached as sd0on successful setup. I usedbioctl -c C -l /dev/wd0a softraid0where-c Cspecifies a device with raidlevel “CRYPTO”,-l /dev/wd0aspecifies the label of type RAID created in step 3 to use for the CRYPTO device, andsoftraid0is the softraid device to configure (this value should work unless you already have asoftraid0device).
exitfrom the shell and(I)nstallas normal, installing to the disksd0(or whichever disk the crypto volume got attached as). In the partitioning dialog, you may need to manually adjust things since the auto-partitioning creates an additional swap label onsd0, which we don’t need given we already havewd0b.- Using
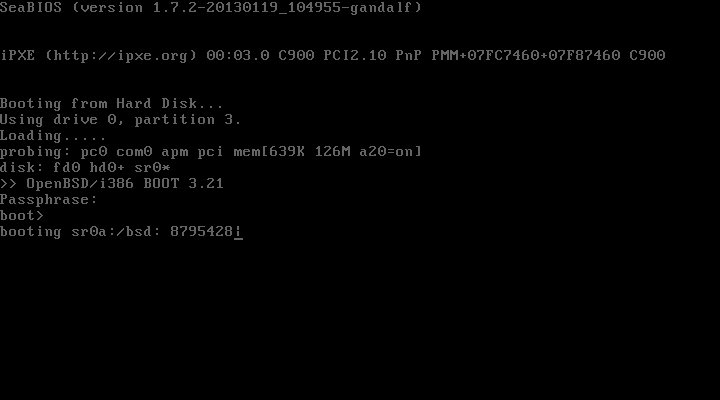
ed(1), add the line1a8bab44e9cc178d.b none swap swto/mnt/etc/fstab, assuming that1a8bab44e9cc178dis the DUID associated withwd0.1 Alternatively, wait until you boot into your system, and add it to your/etc/fstabusingvi(1)ormg(1). - Reboot, and you’ll be prompted for your passhprase. You’re done!
Here’s a screenshot of steps 1 through 4.
Here’s a screenshot of the passphrase prompt, after successfully entering the passphrase:
If I’ve made any errors in the steps above, please point them out in the comments below or by sending me an email.
-
You can find this out by running
sysctl hw.disknames. It will output something likehw.disknames=wd0:1a8bab44e9cc178d,cd0:,[...]. Just search for the DUID associated withwd0. ↩︎
Comments: To comment on this post, send me an email following the template below. Your email address will not be posted, unless you choose to include it in the link: field. If your web browser is configured to handle mailto: links, click comment to load the template into your mail client.
To: Ryan Kavanagh <rak@rak.ac> Subject: [blog-comment] /blog/2013-03-26-setting-up-full-disk-encryption-in-openbsd-5.3/ post_id: /blog/2013-03-26-setting-up-full-disk-encryption-in-openbsd-5.3/ author: [How should you be identified? Usually your name or "Anonymous"] link: [optional link to your website] Your comments here. Markdown syntax accepted.6 Comments
Vadim Zhukov
OpenBSD will automatically pick up swap partition, there is no need for them in fstab. Also, it can be noted that initialization of softraid volume can be done separately, in more friendly than installer’s environment. :)Ryan Kavanagh
Hi Vadim, are you sure about that? I reinstalled going from i386 to amd64, and didn’t specify the swap partition, but OpenBSD didn’t automatically pickup the swap partition outside of the softraid.Neal
Nice Post! Would love to follow your blog but for some odd reason the rss feed does not seem to work. Please can you look into that?Ryan Kavanagh
Sorry, it was an “—” in the HTML source that was screwing up the generated Atom feed; replacing it by a “—” fixed it. Thanks for letting me know! RyanRyan Kavanagh
A “—”, replaced with “—”.Baraka
Vadim is right, step 6 is useless if you init swap on real device, in your example, after sd0 init, choose to init wd0, keep partitions and OpenBSD will do the rest.